Whether you are an employer, a payroll or Human Resources services provider, or an accounting firm, storing and safeguarding employee data or your client’s employee data is imperative. Due to withholding tax and labor law requirements, the array of data required to be maintained often falls squarely into the definition of “personal Information” of state data breach notification laws. Additionally, data breaches not only impact a business’s reputation, potentially damaging the employee/employer relationship, but also may trigger significant legal requirements and open a business to data breach claims or lawsuits.
Data Breaches Can Happen to Any Business
A data breach may occur accidentally. A common source of a data breach is a phishing scam, where an email is sent to an employee who may have access to or easily obtain sensitive employee data, such as names of employees and their Social Security numbers, is targeted. The email may come in the form of an urgent request for the data from a person of authority in the company or as a malicious email with a phishing URL or attachment.
An employee may also willfully release data. In May 2019, the U.S. Department of Justice reported that an employee of a data analytics and risk management firm attempted to sell data on the dark web. The FBI Cyber Task Force and local authorities prevented the breach.
The 2019 Internet Security Threat Report released by Symantec, a leader in cyber security, revealed that 1 in 10 URLs are malicious and in the U.S., 1 in 674 emails is malicious. Smaller organizations, with fewer than 250 employees, received malicious emails more frequently than larger organizations.
Even if internal controls are secure, a data breach of employee data may occur through a third-party vendor. No one is invulnerable, not even the Department of Defense. In October 2018, the Pentagon announced that its travel records system, containing the personal data of 30,000 employees and contractors, was compromised. The data was stored in a system maintained by a third-party vendor.
The government was also hit by two lawsuits filed by members of the American Federation of Government Employees and the National Treasury Employees Union for a 2014 data breach where the birth dates, Social Security numbers, and even fingerprint records were stolen from former, current, and prospective government workers. The data was collected by the Office of Personnel Management (OPM) who provided access to KeyPoint Government Solutions, Inc., a third-party vendor who conducted background investigations. The hackers used KeyPoint credentials to gain access to 21.5 million background investigation records. The hackers also gain access to four million federal employees’ personnel files and approximately 5.6 million sets of fingerprints. Since the 2014 breach, some of the affected individuals have become victims of financial fraud and identity theft, while the remaining individuals remain in fear. The district court dismissed the complaints, however, a federal appellate court has ruled that the individuals have sufficient standing to claim damages under the Privacy Act and OPM’s refusal to employ industry-standard security protocols unlocked OPM’s waiver of sovereign immunity. The court was quick to note that KeyPoint also did not have derivative sovereign immunity because Keypoint’s alleged security faults were directed by the government, and it is alleged to have violated the Privacy Act standards incorporated into its contract with OPM.
The 2019 Internet Security Threat Report released by Symantec, a leader in cyber security, revealed that 1 in 10 URLs are malicious and in the U.S., 1 in 674 emails is malicious. Smaller organizations, with fewer than 250 employees, received malicious emails more frequently than larger organizations.
Once a data breach has occurred, the average time to identify the breach is 197 days and it takes an average of 69 days to contain it, according to Ponemon Institute’s 2018 Cost of Data Breach study.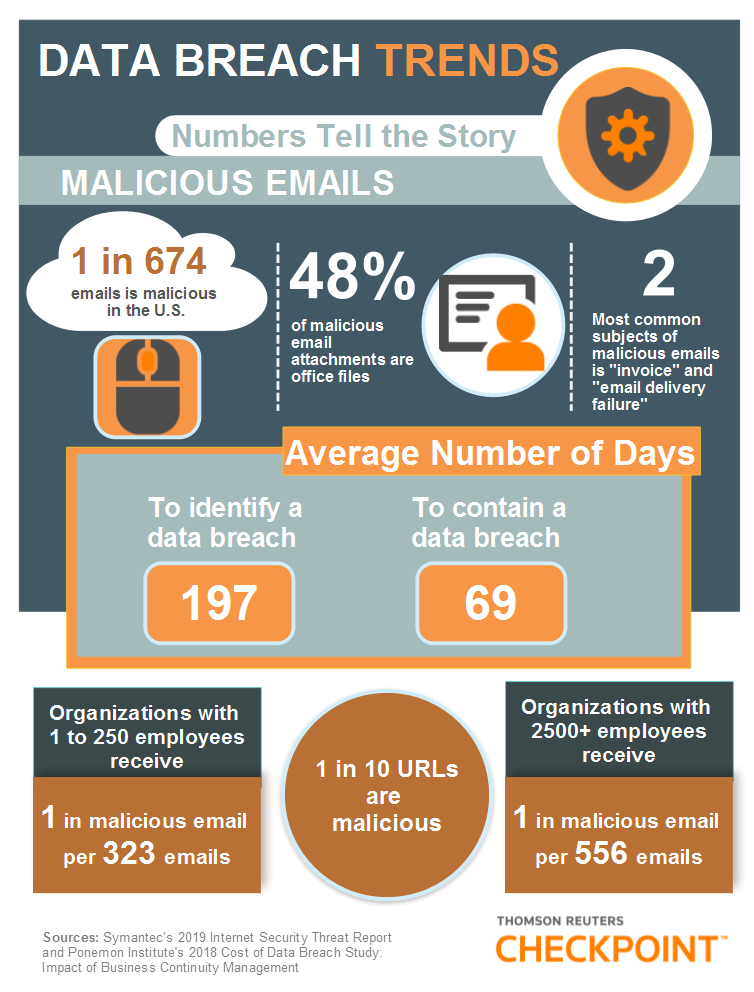
Know State Data Breach Requirements
All 50 states and the District of Columbia have data breach laws that require a business to notify individuals and in some cases, state agencies, of a security system breach resulting in the exposure of “personal information.”
The term “personal information” varies from state to state, however, it will cover, at a minimum, a person name, social security number, driver’s license number, and a financial account number. These are common data elements that can be found in payroll records. Additionally, some states include a Passport number, something that may be recorded on an I-9 form or biometric data such as a fingerprint, retina or iris image, or voice print, that can be a component of a time and attendance system, or health insurance information, something that may recorded for benefits administration purposes.
State data breach laws require a business to provide notification to affected individuals as soon as 30 days of the breach or as soon as reasonably practicable, depending on the state.
The laws will provide the terms of the notice and the delivery method. Some states require state agencies to be notified of a breach such as the state Attorney General when a certain number of state residents are inspected by the breach or in some states, more broadly as, if the business operates in the state.
Some states also require reasonable data security measures, specific data security requirements, and a statute of limitations on data breach claims.
Possible Consequences of a Data Breach
Employees may sue an employer for a data breach with varying success depending on the circumstances and state laws. The suits generally allege breach of duty and negligence for failing to follow industry standards for data protection.
In January 2017, an employee of TransPerfect Global received a “phishing” email requesting W-2 forms and payroll information for current and past employees. The email claimed to be a request from TransPerfect’s CEO. The employee released employee names, addresses, dates of birth, social security numbers, and direct deposit banking information. The employees of TransPerfect alleged that the data breach left them with an “imminent risk of future identity theft” and they claimed that attempting to prevent after the event resulted in lost time and money. The court found that the employer had a duty to protect the personal data of its employees. The Pennsylvania Supreme Court recently came to a similar conclusion.
Beyond potential law suits for breaches, businesses can also find themselves subject to stiff fines and penalties if they fail to follow data breach notification requirements.
Data Security and Collection Check-Up
Employers and businesses responsible for storing employee data should review current data collection and storage processes and procedures.
- What data are you currently maintaining? Is the data crucial or is perhaps data overcollected? What data are you currently collecting that may be eliminated to avoid more data to be possibly breached?
- What is your current data storage method? Is it sufficient? How old are the current security measures in place? Is there room for improvement?
- What is your current method of data disposal?
- Do you periodically assess your systems for vulnerabilities?
- Do you know your state’s data breach laws? What about the data breach laws of states that you currently have employees?
- Is there currently an employee training provided to all employees for best practices to avoid phishing scams, downloads of malware, and other potential data breach threats?
- Who has access to sensitive data and evaluate whether too many employees have access? Are the individuals with access given additional training on possible data breach threats?
- Do you know what security measures are in place to protect your employee’s data by third party vendors such as payroll service providers, CPA firms, or benefits administrators?
- Do you offer credit reporting assistance for victims of a data breach?
- Do you know who to notify if a data breach occurs?
Warning Signs of a Data Breach and What to Do
The Security Summit is a coalition where the IRS, the software industry, tax preparation firms, payroll and tax financial product processors and state tax administrators work together to combat identity fraud and protect taxpayers. The IRS has provided some warning signs of a data breach to tax preparers that may also be applied to any individual or organization that collects payroll date. These warning signs include the sudden receipt of tax transcripts that were not requested, tax professionals or clients responding to emails that the organization or firm did not send, network computers running slower than usual, computer cursors moving or changing numbers without the user touching the keyboard, and network computers locking out employees.
When you have determined that a data breach has occurred, the IRS, FBI, state tax agencies, local police, impacted individuals and credit services should be notified. Check state data breach notification laws to determine what specific further actions are legally required. Businesses should also contact a security expert to figure out how the breach occurred and how many individuals are impacted and what systems were attacked. A security expert may be able to halt the breach and put a plan in place to prevent future breaches. Finally, businesses should contact their insurance company to notify them that a breach has occurred and find out if the policy covers data breach mitigation expenses. The IRS has specific measures for reporting Form W-2/SSN data theft.
The Final Word
Businesses cannot avoid collecting employee data due to the variety of payroll record-keeping requirements, however, businesses can update security systems and protocols, provide employee training, and perform ongoing data security monitoring. A proactive approach may help thwart the headaches of a data breach.
For more information on securing your client’s data, check out Protecting your firm’s client data from cybercriminals and Data security for tax and accounting firms.
Additional Resources:
2019 Internet Security Threat Report by Symantec 2018 Cost of Data Breach Study: Impact of Business Continuity Management Form W-2/SSN Data Theft: Information for Businesses and Payroll Service Providers IRS News Release 2018-177 Federal Trade Commission, Data Breach Response: A Guide for Business






